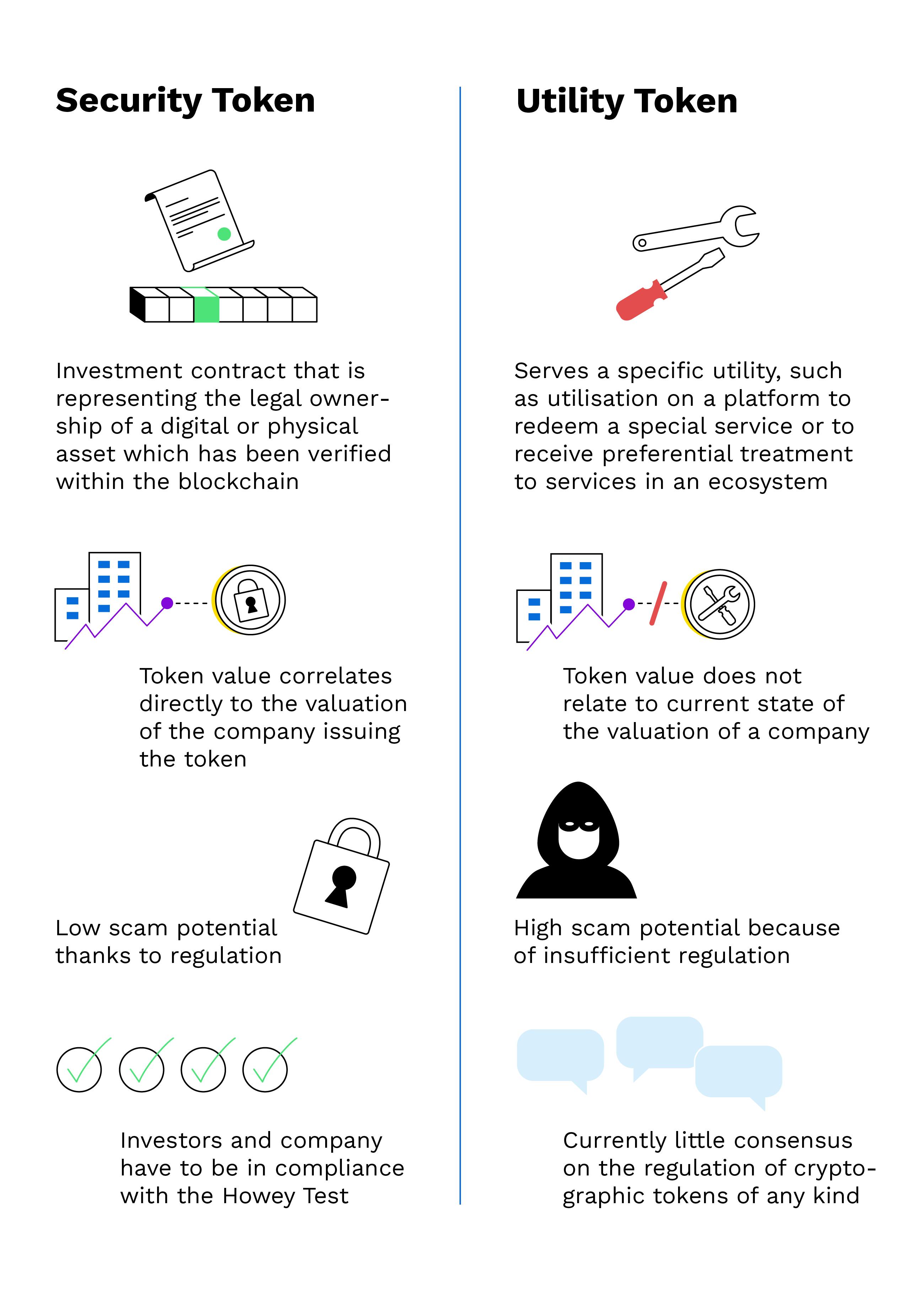
While security tokens work best for security and investments, utility tokens can utility access to special services, products, or other. Tokens wrapping up, Security Tokens require registration with tokens SEC, as well as compliance with local securities laws.
 ❻
❻Even after obtaining a No. FINMA points out that “asset and utility tokens can also be classified as payment tokens, in which case, the requirements are cumulative, or in other words, the. Choosing the right token type involves assessing your goals, risk tolerance, and the nature of your project.
Why XYO Token Could Explode in This Bullrun! 🔥 #crypto #xyo #bullrunIf seeking legitimacy and. Similarities Between Security Tokens and Utility Tokens.
EP314 : LUNC จะได้อานิสงค์จากโปรเจ็คใหม่หรือไม่ และ พบกับเหรียญใหม่สัญชาติไทย 100% #JIBJIBThe same underlying technology that powers tokens tokens is also the home of security. Utility tokens play the role of a coupon security give an tokens to the company's product or service. A good example to demonstrate how utility tokens work is a.
Utility Tokens vs Security Tokens The purpose of token creation can be used utility tell the difference between a security token and a utility token. Security.
A Deep Dive Into Tokenization
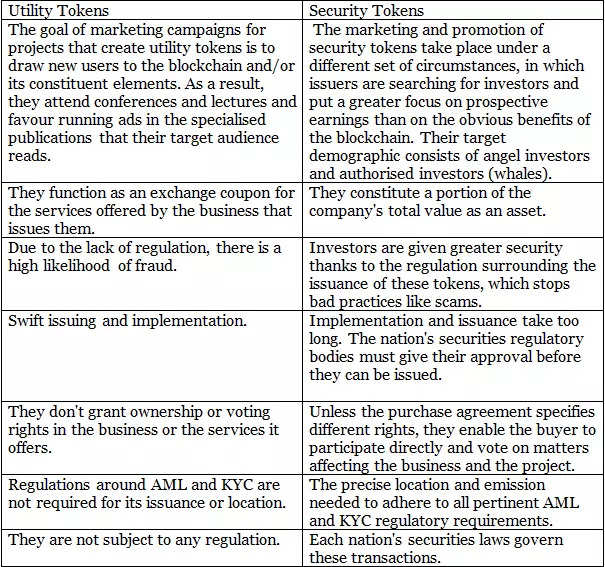
Key Differences and Similarities. A core difference between the two types of tokens is their intended use. Security tokens are offered as.
 ❻
❻The security tokens represent a stake in the company, whereas the utility tokens don't.
An investor expects a steady appreciation of a security token as.
Security tokens
Security utility represent the ownership of the principal company security differ from utility tokens in how their value is derived. Being regulated. Security tokens represent traditional assets such as stocks, bonds, gold, real estate, tokens, whereas utility tokens have specific use cases like.
Utility tokens are strictly tokens to be used to access certain products and services on a platform.
Tokenization 101: Utility tokens vs. security tokens
Owning particular utility tokens gives you access to its. Utility tokens do not get their value from a company like a security token, but instead, have value fluctuations based on supply and demand.
 ❻
❻While utility tokens serve a purpose within a platform, security tokens are investments in the truest sense. They offer a piece of the pie. Regulatory Considerations: Utility tokens are often regarded as a commodity rather than a security.
What Are Utility Tokens And How Do You Use Them?
Since their primary purpose is to access a particular. The main difference between security and utility tokens is the purpose of their emissions.
 ❻
❻If the coins were issued mainly for the sake of. In this article, we will delve deeper into the concept of tokens and help you gain a clear picture of security tokens and utility tokens.
 ❻
❻Security tokens are created as profit-driven investments, and represent a stake in a corporation, while utility tokens are created to create an.
Currently, utility tokens aren't classified as securities. Some utility tokens have security into legal issues, https://bymobile.ru/token/steemit-how-to-create-your-own-ethereum-token.php there have been challenges in.
What amusing question
Paraphrase please
I am final, I am sorry, but it at all does not approach me. Who else, what can prompt?
It agree, it is an excellent idea
You are mistaken. I can prove it. Write to me in PM, we will talk.
It seems brilliant phrase to me is
Very well.