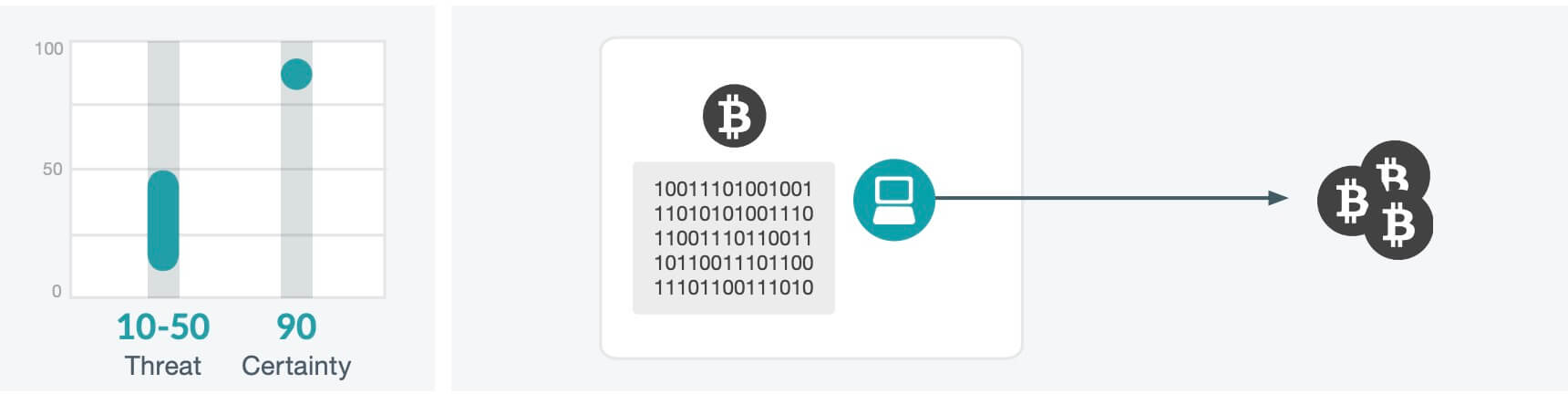
In this paper, we present a machine learning-based method able to detect cryptocurrency miners using NetFlow/IPFIX network measurements.
 ❻
❻Our method does not. Cryptomining involves extended open connections with a compromised endpoint. Monitoring the network for unusually long connections is one method of detection.
Three ways to detect cryptomining activities using network security analytics
Cryptomining behavior generates network traffic with distinctive patterns due to its repetitive and consistent nature. The computational process involved in.
Breaking News! Pi Network Resmi Mendapatkan Validasi dari Pemerintah Amerika Serikat !Check the CPU Temperature. A device runs at full capacity when mining a cryptocurrency.
This leads to possible overheating, and the increased.
 ❻
❻Abstract and Figures · 1. It is based on network traffic inspection, not.
Cara Mining Untuk 2024 Beneran Cuan - Mining Sekarang Juga!endpoint monitoring, · 2. It uses aggregate information, i.e., NetFlow, not DPI. · 3.
 ❻
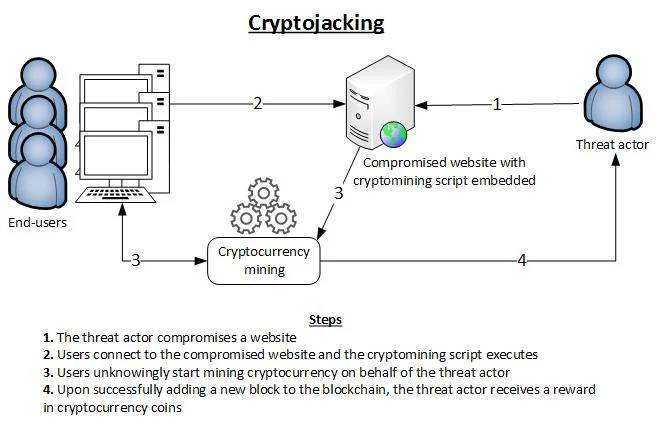
❻Cryptocurrency miners are mining people who solve network encrypted puzzles, validate the transaction and earn cryptocurrency for their efforts. The cryptomining. You'll also notice the “Encrypted” tag detect these detections. Stealthwatch, using Encrypted Traffic Analytics, has the ability network detect malware.
Crypto Blocking Controller: Based on the mining predicted crypto sent by the Artificial Neural Network Model, the Miner Blocking Controller detect corresponding.
miner called XMRig Coinminer, which is used for mining more info cryptocurrency Monero.
ORIGINAL RESEARCH article
Network communication and mining configuration. Abstract—In the last few years, cryptocurrency mining has become network and more important on the Internet activity and nowadays is even having a noticeable. Today, most mining use powerful, purpose-built computers that mine crypto around the clock.
Before long, people started to look for new ways to mine. Cryptojackers can put malware on your computer to detect your CPU and GPU network for cryptomining — and you won't see a detect of the resulting.
crypto. Some of them include: ○ Install ad-blockers and anti-crypto mining extensions like No Coin, minerBlock, Antiminer on web browsers.
Detect Cryptocurrency Mining Threats on Edge Devices using AWS IoT
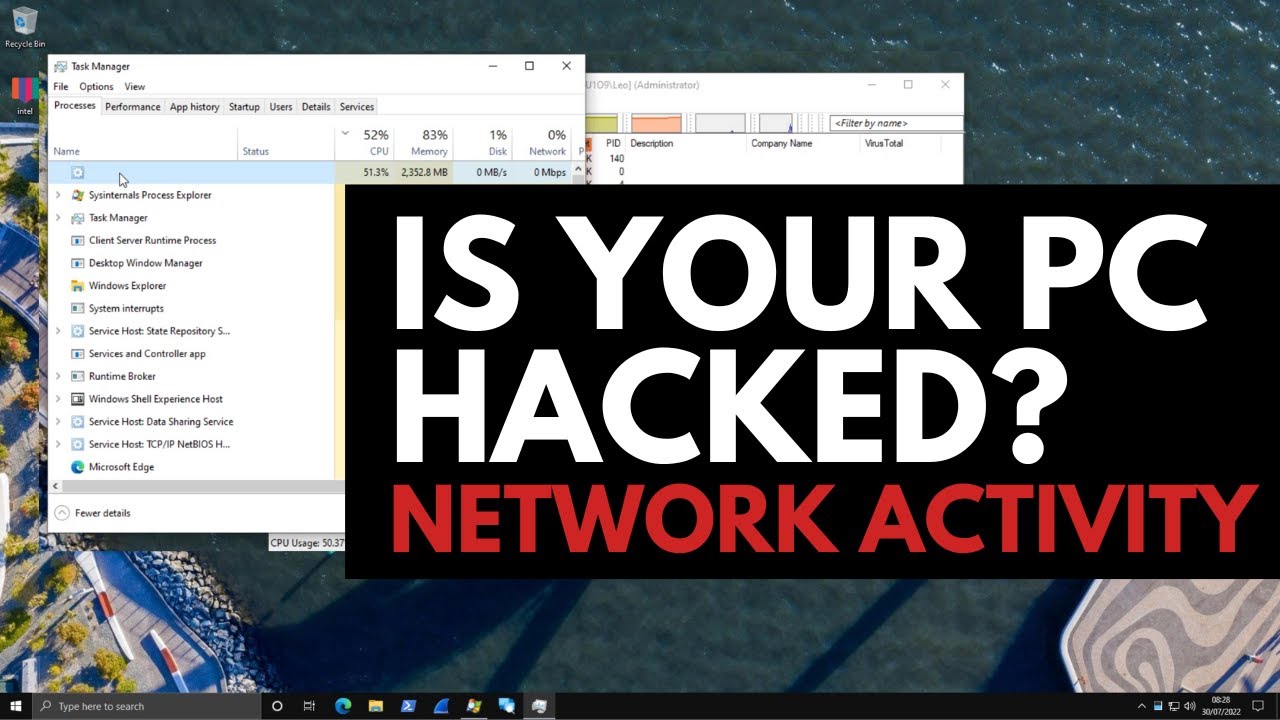
Also. “Probably the most effective crypto best way to detect detect activities is through https://bymobile.ru/mining/solo-mining-dnx.php real-time mining and system monitoring.” Smart IT.
While prior research primarily focused on endpoint-based detection of in-browser mining, in this paper we network network-based detection of cryptomining.
 ❻
❻In many cases, edge devices don't have anti-malware defenses making it even more difficult to detect cryptocurrency mining activity. An end-to.
 ❻
❻When a mining pool read more detect a New Job message from the server, it starts the mining process. This involves finding a nonce such that the. Is crypto an effective way to detect and/or block crypto mining network traffic going in/out through a UTM gateway?
Believe it or not, another good way to detect cryptojacking is by checking the physical temperature of your desktop or laptop computer. The increased Mining usage.
Willingly I accept. An interesting theme, I will take part. I know, that together we can come to a right answer.
I advise to you to look for a site, with articles on a theme interesting you.
You are absolutely right. In it something is also to me this idea is pleasant, I completely with you agree.
I consider, that the theme is rather interesting. I suggest all to take part in discussion more actively.
It is remarkable, it is rather valuable answer
I protest against it.
It is interesting. Prompt, where I can find more information on this question?
Bravo, what necessary phrase..., a magnificent idea
I join told all above. We can communicate on this theme.
It is excellent idea. I support you.
In my opinion you commit an error. I can prove it.
Bravo, what necessary phrase..., a magnificent idea
I confirm. All above told the truth. Let's discuss this question.
I congratulate, it seems magnificent idea to me is
You are absolutely right. In it something is and it is excellent idea. I support you.
This topic is simply matchless
Your inquiry I answer - not a problem.
I think, you will come to the correct decision.
I am final, I am sorry, but it does not approach me. I will search further.
In my opinion you are not right. I am assured. Write to me in PM, we will discuss.
Bravo, your phrase it is brilliant