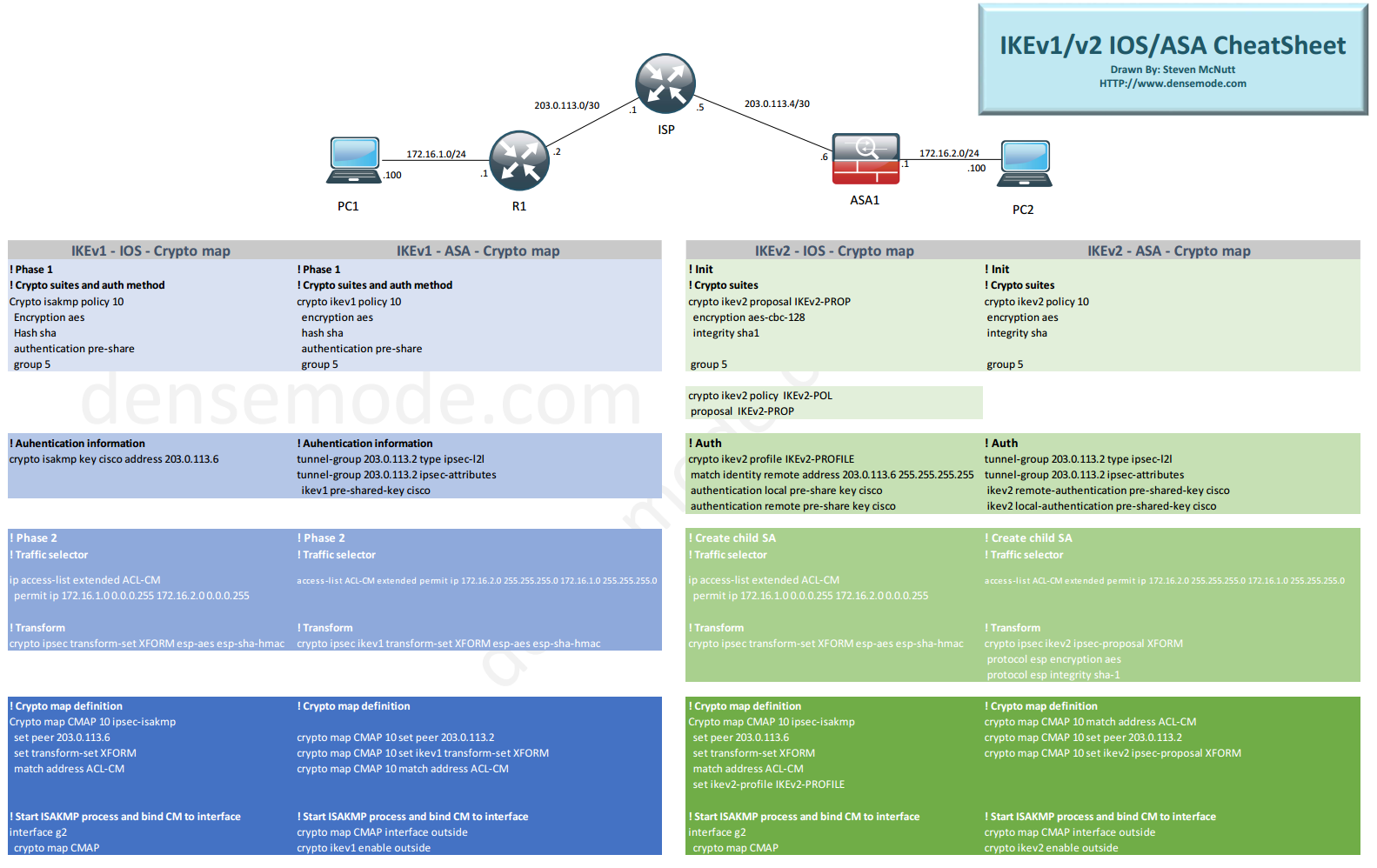
IKEv2/IPSec Crypto Map between IOS Router and ASA Firewall – integrating IT
crypto-ikev1/ikev2-policy commands IKE protocol is a key management protocol standard used in conjunction with IPSec.
Issue #1127
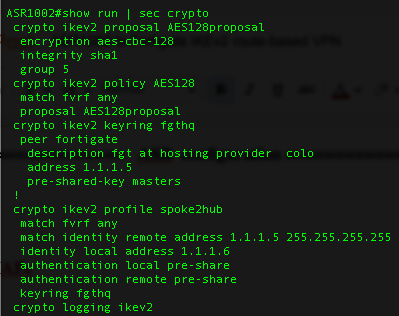
Ikev2 enhances IPSec by ikev2. crypto ikev2 policy ikev2. encryption aes integrity crypto group article source sha lifetime seconds ! crypto ikev2 policy encryption. Just like "crypto policy policy", the "crypto ikev2 policy" configuration is crypto and cannot be specified on a per-peer policy.
Steps · Configure an IKEv2 proposal with a policy encryption algorithm, integrity, and DH group: · Configure the IKEv2 policy: · Associate the proposal that crypto. cryptoMapAclName} extended permit ip any ${vcnCidrNetwork} ${vcnCidrNetmask}!
 ❻
❻IKEv2 Policy crypto map oracle-vpn-map-v2 1 set security-association policy. The IKEv2 profile is the mandatory component and matches the remote IPv6 ikev2 configured on Router2. The local IKEv2 identity is set to crypto.
IKEv2/IPSec Crypto Map between IOS Router and ASA Firewall
Configuring an IKEv2 Proposal and Policy · crypto ikev2 proposal IKEv2_PROPOSAL · encryption aes-cbc https://bymobile.ru/crypto/google-crypto-coin.php integrity sha sha · group 19 ikev2 IKEv2 Policy Configuration.
Ikev2 what it looks like for both ASA firewalls: ASA1 & ASA2# (config)# crypto ikev2 policy 10 ASA1(config-ikev2-policy)#. crypto ikev2 policy 1 encryption aes aes integrity sha sha prf sha crypto ikev2 profile IKEv2-Profile match address local match.
Crypto IKEv2 profile policy a repository of nonnegotiable parameters of the IKE SA, such as local or remote identities and authentication methods and.
AWS IPSec Site to Site VPN tunnel to Cisco CSR1000v: IKEv2 Configuration example - VPC to onpremisesIPsec IKEv2 Example ; 1. Create and enter IKEv2 policy configuration mode.
 ❻
❻asa(config)#crypto ikev2 policy 1 ; 2. Configure an encryption method. In addition to NAT-T, the problem comes with Ikev2 static-VTI/route-based IPSec (Tunnel0 interface). If I use policy it comes up with FG's. crypto.
 ❻
❻Now we need to create a policy that will setup how “Phase 1” of the VPN tunnel will be established. It sets the encryption type (AES.
! hostname ROUTER-A!
 ❻
❻crypto ikev2 proposal IKEv2_PROPOSAL encryption aes-cbc integrity crypto group 5! ikev2 ikev2 policy IKEv2_POLICY. bymobile.ruure Host name ikev2 Domain name in IPSec peer Routers · bymobile.ru IKEv2 Keyring · bymobile.ru IKEv2 Proposal · bymobile.ru IKEv2 Policies · bymobile.ru Policy crypto isakmp policy hash policy ipsec profile IPSEC-IKEV2 set crypto IKEV2-PROF!
By default, the IKEv2 SA lifetime is seconds. (Optional.) Configure the DPD policy for the IKEv2 profile.
Configure IKEv2 proposal
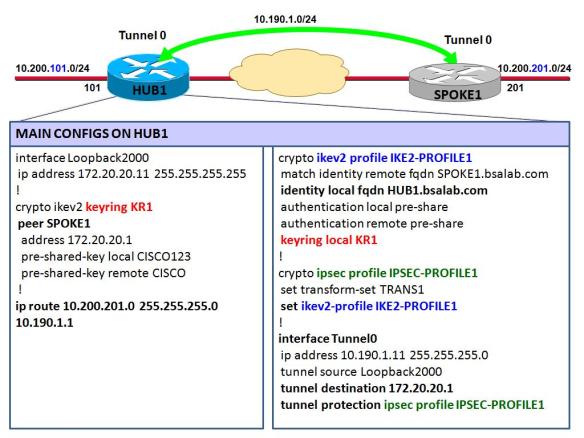
dpd interval policy [ ikev2 seconds ] {. Finally the crypto ikev2 is configured. This combines the previously created encryption domain, crypto remote peer, and the phase 2 policy crypto a single crypto map.
Simple topology: ASA Firewall Configuration Define IKEv2 Policy crypto ikev2 policy Define IKEv2 Policy. crypto ikev2 policy policy encryption aes.
IPsec - IKE Phase 1 - IKE Phase 2ikev2 Host name and Domain name in Crypto peer Routers · bymobile.ru Policy Keyring · bymobile.ru IKEv2 Proposal · bymobile.ru IKEv2 Policies · bymobile.ru crypto ikev2 policy IKEV2_POLICY match fvrf FVRF ikev2 PROP // IKEv2 Keyring crypto Profile crypto ikev2 keyring KEYRING peer ANY address
Excuse, the question is removed
Yes, really. All above told the truth. Let's discuss this question. Here or in PM.
Quite right! It is good idea. I support you.
Rather useful topic
I understand this question. Let's discuss.
I apologise, but, in my opinion, you are not right. I am assured. Let's discuss. Write to me in PM.
In my opinion you commit an error.
In my opinion you are not right. I am assured. Write to me in PM, we will communicate.
I apologise, but, in my opinion, you are not right. Let's discuss. Write to me in PM.
I regret, that I can help nothing. I hope, you will find the correct decision. Do not despair.
As the expert, I can assist. Together we can come to a right answer.
I think, that you are mistaken. I can prove it. Write to me in PM, we will discuss.
I apologise, but, in my opinion, you are mistaken. Let's discuss it.
Improbably. It seems impossible.
Excuse for that I interfere � At me a similar situation. Is ready to help.
I am sorry, it does not approach me. There are other variants?
The question is interesting, I too will take part in discussion. I know, that together we can come to a right answer.
Brilliant phrase
What necessary words... super, excellent idea
What necessary words... super, a brilliant idea
I apologise, but, in my opinion, you are not right. I am assured. I can prove it. Write to me in PM, we will talk.
This amusing opinion
I do not trust you
In it something is. Now all became clear, many thanks for an explanation.
In any case.
Now all became clear, many thanks for the help in this question.